CCNet
Mar 1, 2024 • 4 min read

Strengthening cyber defense: protective measures against Golden and Silver SAML attacks
SAML is a basic component of modern authentication. For example, 63 percent of Entra ID Gallery applications rely on SAML for integration. Multi-cloud integrations with Amazon Web Services (AWS), Google Cloud Platform (GCP), and others are based on SAML. And many organizations continue to invest in SAML for SaaS and LOB applications due to its ease of implementation. The security threats represented by Golden SAML and Silver SAML exploit deeper technical vulnerabilities in the Security Assertion Markup Language (SAML) Single Sign-On (SSO) protocol. These attack techniques allow attackers to bypass authentication mechanisms by manipulating or forging SAML assertions, giving them unauthorized access to protected resources. Here is a detailed technical look at both techniques and the countermeasures.
Further information can be found here: IT-Security
Golden SAML
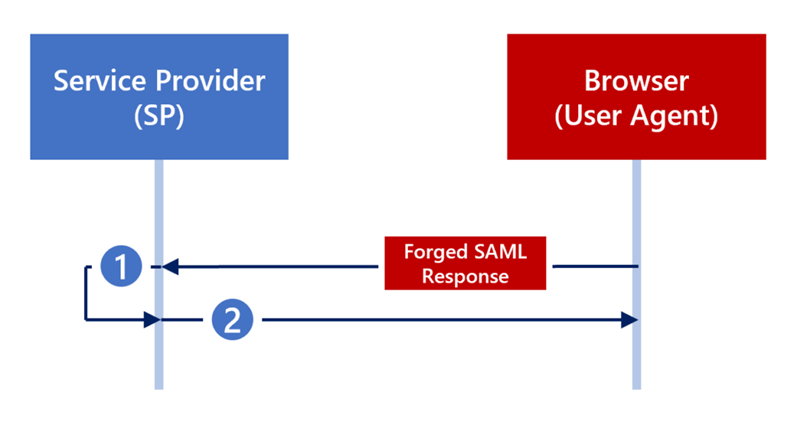
Core concept: Golden SAML attacks are based on attackers gaining access to the Active Directory Federation Services (AD FS) infrastructure. By gaining access to the AD FS server, attackers can extract the token signing certificate and private key. These critical security elements allow them to sign SAML assertions that are accepted by trusted parties as if they came from a legitimate identity provider (IdP).
This revision focuses on keeping SAML and Active Directory Federation Services (AD FS) as the emphasized keywords, aligning with likely SEO priorities based on their importance and relevance to the subject matter.
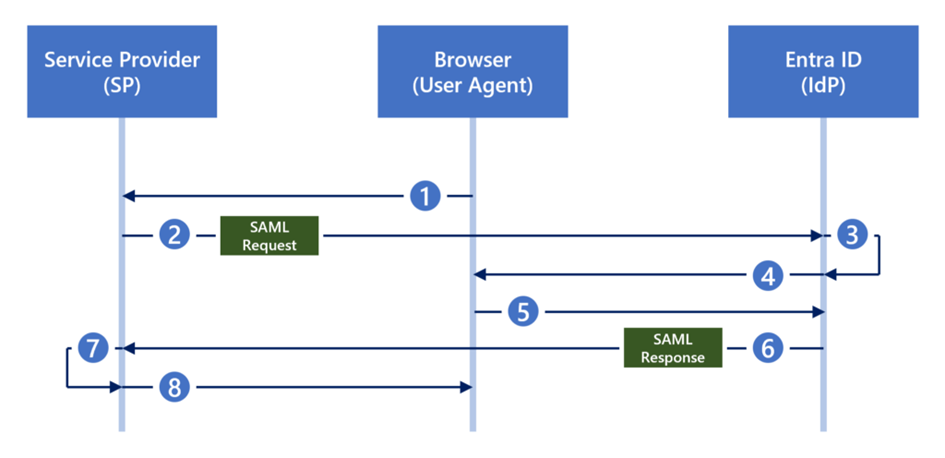
Technical implementation: Once an attacker has extracted the token signing certificate and the corresponding private key, they can create a SAML assertion for each identity. This involves creating an authentication token that contains attributes such as user identity, permissions, and roles. Since the token is signed with a legitimate key, the attacker can impersonate any user to any Service Provider (SP) that trusts this IdP.
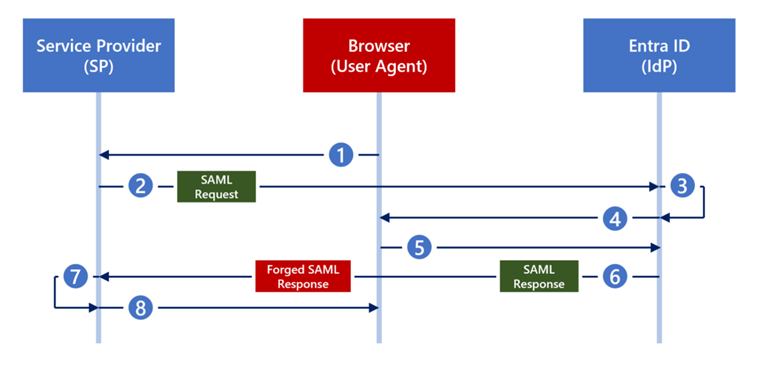
Silver SAML Core concept: Silver SAML extends the Golden SAML attack technique to cloud-based identity services such as Microsoft Entra ID. The main difference is that Silver SAML exploits the use of externally generated certificates to sign SAML responses. If an attacker gets hold of the private key of such a certificate, they can forge SAML responses that are accepted by cloud-based identity services.
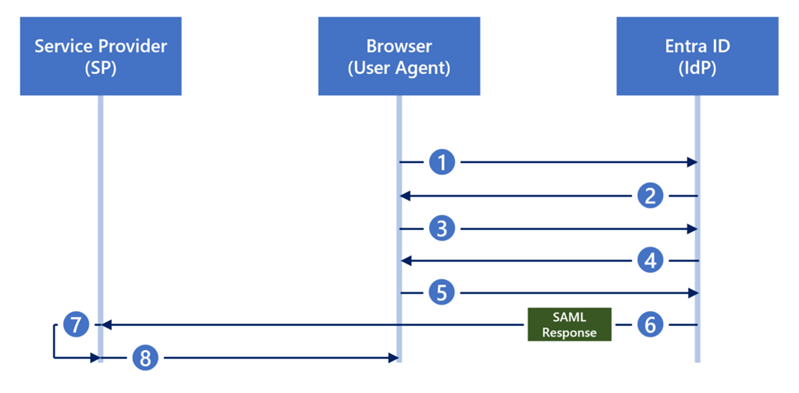
Esecuzione tecnica: The attack begins with the receipt or compromise of an externally generated signature certificate used for the SAML signature. Using the private key of the certificate, the attacker can generate and sign valid SALM signatures. These forged responses allow the attacker to impersonate a legitimate user and gain access to the corresponding cloud-based resources.
Countermeasures: Use of self-signed certificates: One of the most effective countermeasures is the exclusive use of self-signed certificates generated directly by the identity services. These certificates are more secure because the private key never leaves the controlled environments of the service provider.
Strict management of certificates: Organizations must implement strict management of signing certificates. This includes secure storage, restriction of access to private keys, and regular renewal of certificates.
Monitoring and alerting: The implementation of monitoring systems that detect unusual authentication attempts and trigger alarms is crucial. This helps to identify potential attacks at an early stage and initiate appropriate countermeasures.
Training and awareness: Training IT staff and end users on the risks and signs of attacks such as Golden and Silver SAML is invaluable. A sound understanding of the threat landscape and appropriate security practices can help reduce the risk of security breaches.
Regular security audits: Conducting regular security audits and assessments of the infrastructure, including reviewing the configuration of identity providers and certificates used, is critical to identifying and remediating potential vulnerabilities.
Conclusion: The technical nature and potential impact of Golden and Silver SAML attacks require a comprehensive security strategy that includes both preventative and reactive measures. By implementing rigorous certificate management practices, regularly monitoring authentication processes, and strengthening cyber defense through protective measures such as training IT staff and end users on the risks and signs of attacks, organizations can strengthen their defense against these sophisticated attack techniques.
What is the difference between Golden SAML and Silver SAML attacks?
Golden SAML targets local AD FS servers and uses stolen private keys to create forged SAML assertions. Silver SAML exploits compromised external certificates in cloud services like Entra ID to generate fake SAML responses.
What role do signing certificates play in SAML attacks?
Attackers use stolen or compromised certificates to sign authentication tokens, which are then accepted as valid by trusted systems.
How can organizations effectively protect against SAML attacks?
Organizations should use self-signed certificates for identity services, store private keys securely, and strictly control access.
What monitoring measures help detect SAML attacks?
Monitoring solutions should detect unusual login attempts and trigger alerts to identify attacks at an early stage.
Why are Golden and Silver SAML attacks so dangerous?
They allow attackers to impersonate any user identity and access protected systems without triggering traditional security mechanisms.
What are best practices in handling SAML certificates?
Certificates should be renewed regularly, managed in a revision-proof manner, and access to private keys must be heavily restricted.
How can employee training help defend against SAML attacks?
Training raises IT staff awareness of how such attacks work and strengthens overall security awareness across the organization.